May 19, 2020 brought another colossal vulnerability in the public eye. An Isreali team of academic researchers, from Tel Aviv University and Interdisciplinary Center of Herzliya, released an interesting discovery. The details include a DDoS amplification attack that has organizations like Google working actively to prevent it.
The flaw is broadcasted as NXNSAttack, which impacts the DNS protocol that can be abused to launch a large magnitude distributed denial of service (DDoS) attack, and subsequently can take down targeted websites.
This new research comes from a cyber-security enthusiast group of researchers, namely:
- Researcher: Lior Shafir, PHD Student, Tel Aviv University
- Supervisor: Yehuda Afek, Professor, Tel Aviv University
- Supervisor: Anat Bremler-Barr, Professor, The interdisciplinary Center, Herzliya
What is a DDoS Attack?
Before we move on, let’s clear our basics. A Distributed Denial of Service attack is a powerful weapon against websites and servers. This is done by exhausting them with higher traffic than they can handle, thus ultimately knocking them down. A typical DDoS attack can be achieved by flooding the targeted system with connection requests, messages or fake packets, incoming from multiple sources. This can also be attempted from a small number of computers to create a large scale impact.

What is NXNSAttack?
A NXNSAttack is a flaw in the DNS delegation process that exploits recursive DNS servers. The vulnerability really comes from how DNS servers manage the recursive queries.
To simplify, when you type in a domain name in the address bar, it is the DNS who is responsible for translating this text into IP addresses. But a recursive DNS lookup is when one DNS server communicates with multiple DNS servers to locate an IP address.
Furthermore, these conversions occur on authoritative ‘upstream’ DNS servers that hold a list of DNS records and are the main centers to carry out these requests. These authoritative servers can also choose and delegate similar operations to a ‘downstream’ alternate server like your ISP (Internet Service provider). This delegation of powers became the root cause that hackers misused to magnify the DDoS attacks.
Now coming back to our topic and connecting all the dots, a NXNS attack occurs when a hacker sends a single malicious request to trick an innocent DNS server into running thousands of requests all at once.
This amplified mechanism allows the attacker to bring down a big chunk of the internet with a handful of devices. The official research paper details how a threat actor can manipulate a recursive DNS using a hacked DNS to create a massive surge on a target server and finally crash it indefinitely.
How NXNSAttack Works
For a better understanding, we’ll take the same instance that the researchers have used to beautifully explain the NXNSAttack. But before that, refer the figure below to comprehend the conventional DNS hierarchy structure:

Now, let’s go through the steps below to understand the major flow of how NXNS Attack works
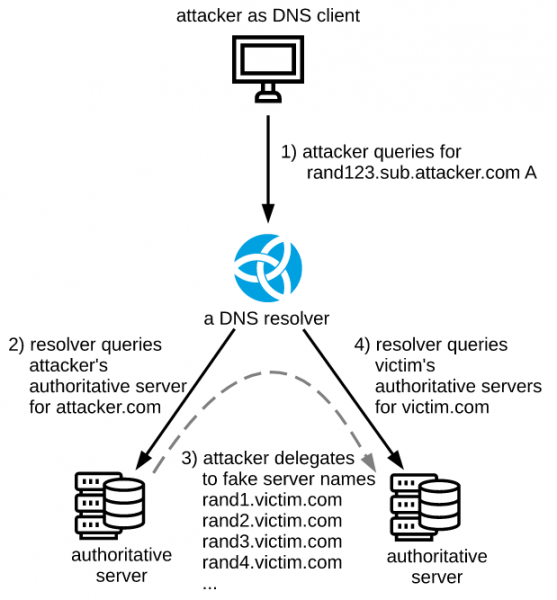
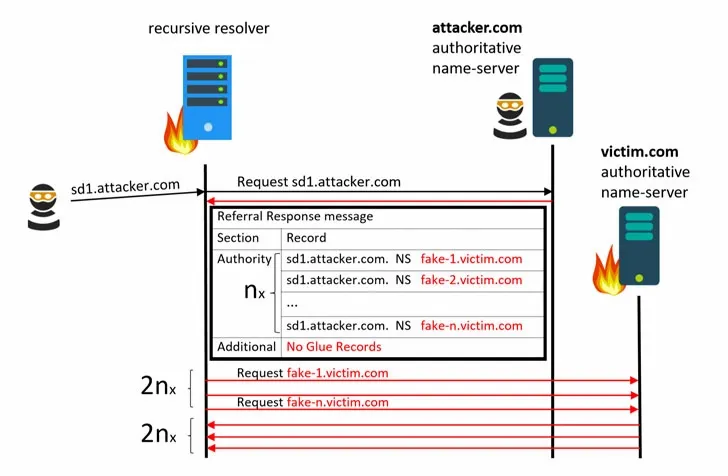
Step 1: The threat actor deploys his own DNS Authoritative Server, and hosts the DNS record for is own domain, i.e. www.attacker.com
Step 2: Now he sends a query for attacker.com to the recursive (or resolving) DNS server.
Step 3: Because the resolving server doesn’t have a matching record to resolve this domain name, it further sends the request upstream and eventually lands on the attacker’s Authoritative DNS server.
Step 4: Now, this malicious DNS responds back saying it doesn’t have the requested domain, and instead gives a list of name servers who might have the said records. The said list consists of a huge number of fake subdomains for the target website, let’s say www.victim.com.
Step 5: The recursive DNS server, upon receiving the reply, transmits DNS query for all listed subdomains, thus flooding the victim authoritative name server.
The final Step 5 above is a well-thought and successfully-executed attempt at DDoS attack.
NXNSAttack Amplification – Real-world Impact
The brains behind this research have proved that creating a high scale surge in any target website, will naturally lead to the associated server crash. Such explosive ‘NXNSAttack’ DDoS attack can blow out of proportion from 2 to 1620 times the original size.
Though a guarded server would most likely be able to detect and block a single malicious DNS behind any DDoS attack, the NXNSAttack provides the hacker the opportunity to misguide with multiple domains and elongate the timeline.
Moreover, as Shafir explains,
"When you try to attack a root server, the attack becomes much more destructive. We cannot prove that they can be knocked down because they're very strong servers, but the amplification is very high and these are the most important assets. Parts of the internet would not work at all in this worst case."
How to Fix Massive DDoS Attack? – NXNSAttack Patch
It’s scary to think how easily any wanna-be hacker can take advantage of this situation, with a couple of devices, a few dollars to set up the server and automated DNS queries.
Luckily, the responsible research team behind the discovery of NXNSAttack started notifying relevant corporations as early as in the beginning of 2020. The checklist included major DNS providers like Google, Amazon, Microsoft, Cloudflare, IBM, other DNS software and CDN providers for mitigation purposes.
Affected softwares include:
- ISC BIND (CVE-2020-8616),
- NLnet labs Unbound (CVE-2020-12662),
- PowerDNS (CVE-2020-10995), and CZ.NIC Knot Resolver (CVE-2020-12667)
- Other commercial DNS providers such as Google, Microsoft, Amazon, Cloudflare, Oracle, IBM Quad9, Verisign, ICANN
The good news is that numerous patches have been released by concerned organizations in the past month, while some are still continuing to address the issue. The world soon realized and accepted NXNSAttack as a real challenge and are working through to address its issues.
If you’re a server administrator, we recommend you must go through the detailed documentation of the Israeli researchers and fix DNS resolvers as soon as possible.

