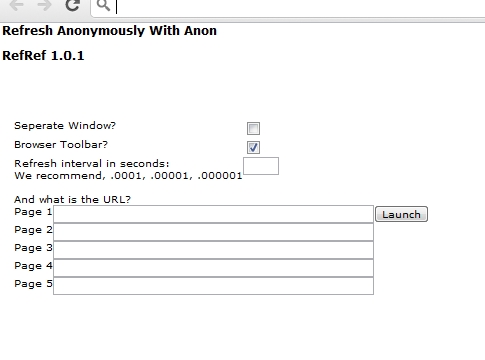
#RefRef - Denial of Service ( DDoS ) Tool Developed by Anonymous
Anonymous is developing a new DDoS tool which is said to exploit SQL vulnerabilities to support the group's future campaigns. So far, what they have is something that is platform neutral, leveraging JavaScript and vulnerabilities within SQL to create a devastating impact on the targeted website. Previously, Low Orbit Ion Canon (LOIC) was the go to weapon for Anonymous supporters during various Operations .However, LOIC is also the reason scores of people have been arrested in the last year, so many feel its time is at an end.
****NOTE*****
Well there is an important point to keep in mind while using this tool. This tool cannot be used against any website or any database server. This tool actually uses the SQLi vulnerability of database server and use the servers own resources to bring the website down. MySql is the prime target of this tool.
Once the downloading is complete, you will need a perl compiler to run the script. You can download it from
Once you are done with the installation of perl , you can check weather it is working fine or not. go to command prompt and type thefollowing command
perl -v
You will see lot of information about perl. This will ensure that perl is working fine. Now place the downloaded script in any directory. In my example I have kept it in my d drive.
Now change your working directory to the directory where you saved the script. Now execute the following command.
perl refref.pl HACK URL
Here Hack URL is the URL you want to target. The URL should be the link that executes some query on the database server.
According to Developer "RefRef is a revolutionary DoS java site. Basically, by using an SQL and .js vulnerability, you can send a page request packet from your home computer with embedded .js file, because of the vulnerability in the SQL/Javascript engine on MOST websites, the site actually TEMPs the .js file on its own server. So now the .js is in place on the host of the site. Next since you still have the request, it picks up the .js file, and all of the requesting for packets power happens on the server, not the requestee. I send two packets from my iphone, and everything else happens on the server. Basically eats itself apart, because since both are on the server, its all a local connection.
"
The new tool, called #RefRef, is set to be released in September, according to an Anon promoting it on IRC this afternoon. Developed with JavaScript, the tool is said to use the target site’s own processing power against itself. In the end, the server succumbs to resource exhaustion due to #RefRef’s usage. An attack vector that has existed for some time, resource exhaustion is often skipped over by attackers who favor the brute force of a DDoS attack sourced from bots or tools such as LOIC.
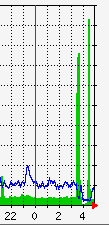
The tool is very effective, a 17-seconds attack from a single machine resulting in a 42-minute outage on Pastebin yesterday. As expected, the Pastebin admins weren't very happy with their platform being used for such tests and tweeted "Please do not test your software on us again."
The effectiveness of RefRef is due to the fact that it exploits a vulnerability in a widespread SQL service. The flaw is apparently known but not widely patched yet. The tool's creators don't expect their attacks to work on a high-profile target more than a couple of times before being blocked, but they don't believe organizations will rush to patch this flaw en masse before being hit.
This means there are a lot of possible targets out there that will be hit at least once. "This tool only makes you vulnerable if you don't keep your systems patched, perform the basic security, which is how Sony got caught with it's pants down," the RefRef developers said.
The tool works by turning the servers against themselves. It sends malformed SQL queries carrying the payload which in turn forces the servers to exhaust their own resources. However, the tool's GUI does have a field for inputting the refresh interval so it might combine traditional forms of HTTP hammering with the new technique.
Some security experts have been skeptical that the success of Anonymous's DDoS attacks can be explained through LOIC alone. They proposed that some of the group's supporters also have access to botnets, a theory that has partially proven to be correct.