For anyone not familiar, ‘Remote Desktop Protocol’ (or commonly referred as RDP) is one of Microsoft’s popular software, that helps connect your computer to another via a network connection. The communication is established through RDP client and server softwares on both systems respectively. Except for Microsoft Windows, it is also available for MacOS, Linux, Unix, iOS and Android.
RDP has been under the cybersecurity experts radar for the past couple of years, mainly because of CheckPoint’s famous revelation on Reverse RDP exploit. It’s research wing has been actively investigating RDP’s weaknesses where hackers could access remote machines and accounts to get their hands on valuable information. But the shocking twist of Reverse RDP changed the game completely.
To understand Reverse RDP attack by ‘Checkpoint’, let’s take an example of a company staff member who’s trying to access a remote (server) machine within the office premises, which has been infected by a RDP malware. So when the said employee will establish connection, the infected PC will attack back on the client PC. This is a traditional Reverse RDP attack, as instead of the client, the remote machine is controlling the process. Let’s take a look at the original Reverse RDP demo by CheckPoint below:
Check Point first brought these issues to light as Part 1, in February, 2019 and Part 2, in August, 2019. This study revolved around numerous critical vulnerabilities in Microsoft, rdesktop and FreeRDP and were reported as
- 26 vulnerabilities (as seen in the screencap below)
- Path Transversal: Guest-host Virtual Machine escape in Hyper-V environment

Microsoft Reverse RDP Patch(es)
Soon after CheckPoint informed Microsoft, and submitted their research in the Black Hat Security conference, Summer 2019, the corporate giant released the patch for issue CVE-2019-0887. But after further analysis, the CheckPoint team found that they could bypass the fix, as the updated version still contained loopholes for the attacker to recreate the earlier exploit. This prompted Microsoft to roll out an updated patch CVE 2020-0655 in February, 2020. Upon initial review, this patch was much more effective to resolve Reverse RDP Windows attack and the issue was closed for then. But the brains behind these vulnerabilities didn’t stop poking around to ensure RDP’s complete security.
On May 14, 2020 CheckPoint disclosed additional vulnerability that the February, 2020 patch was not able to fix. The latest RDP exploit is related to a Windows’ API function ‘PathCchCanonicalize’, which was introduced by Microsoft in the 1st Reverse RDP patch. This action is supposed to provide validation and security to applications against Path Transversal attacks.
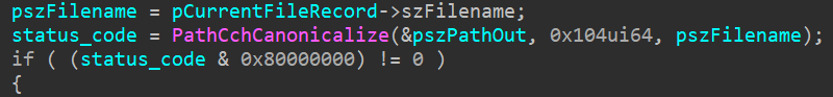
Microsoft Reverse RDP Client Canonicalization Flaw
In the events leading up till now, CheckPoint eventually identified that the problem lies in the cannocalization function that is ideally meant to sanitize file paths. Technically, this new issue allows attackers to access the client and server clipboard synchronization and drop arbitrary files on the client’s device.
To put it in simple words, RDP offers a clipboard feature which can be compromised during a connection between a client and bad server, and used for copying malicious files on Client machine – to achieve RCE (Remote Code Execution.
Additionally, the Reverse RDP patch can be exploited by altering the path. Best coding practices encourage you to validate paths with a unique address. But here the path was simply bypassed by switching backslashes (\) with forward slashes (/). This failure by Microsoft has now allowed threat actors to carry out path-traversal attacks.
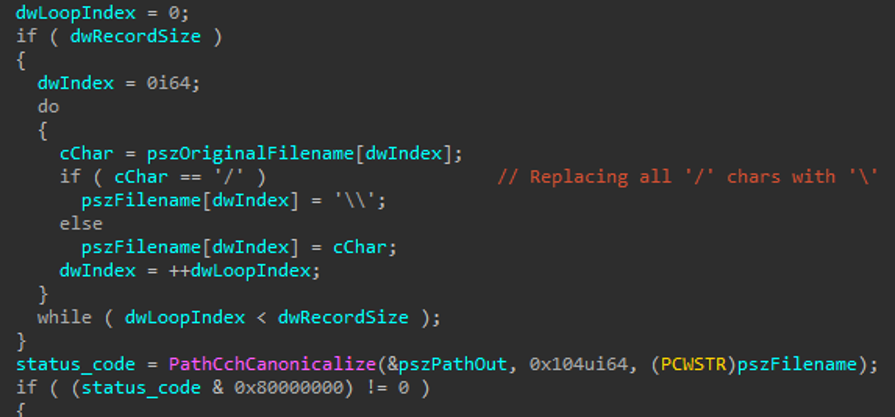
Omri Herscovici, Research Team Leader from CheckPoint explained,
"In CVE-2019-0887, Microsoft tried to solve the path traversal with PathCchCanonicalize without realizing it can be bypassed. In CVE-2020-0655, Microsoft addressed the '\' issue independently in the RDP handling code, without fixing the PathCchCanonicalize function."
In such attacks, the hacker tricks a computer application into leaking sensitive contents. Without the above mentioned canonicalization security, the cyberattackers will be able to access valuable information, and further modify crucial files.
Is RDP Secure? – Latest Update on Reverse RDP Vulnerability / Exploit
If you’re using a 3rd Party RDP Client, then you’re most likely exposed to the “Path Transversal” flaw.
Summarizing the above findings, the latest Microsoft patch only focused on fixing their official client flaws, but conveniently left the 3rd Party RDP Clients exposed. During any remote connection, your critical files are at risk, as the attacker can easily access, read and modify them.
Though the Microsoft team has been informed of this latest vulnerability, they haven’t released any patch yet, and neither are they offering any explanations for this.
Meanwhile, CheckPoint urges the affected users to “manually apply a patch against it” in the relevant programs.

