During Microsoft’s March 2020 security updates patch, they accidentally released a critical security vulnerability that impacted Windows 10 machines. Commonly known as ‘SMBGhost’ or sometimes as ‘EternalDarkness’, it’s a wormable RCE vulnerability (CVE-2020-0796). This flaw was found in SMBv3 (Server Message Block, v 3.0) network communication protocol while handling certain requests.
SMBGhost vulnerability can be exploited against a client or a server to gain code execution privileges. To explain in a nutshell,
- For a server attack, the threat actor has to send a maliciously crafted packet to the victim SMBv3 server
- For client attack, the threat actor needs to set up a malicious SMBv3 server and get the victim user to connect to it
Before jumping onto SMBleed, let’s take a deeper look into SMBGhost with this PoC (Proof of Concept):
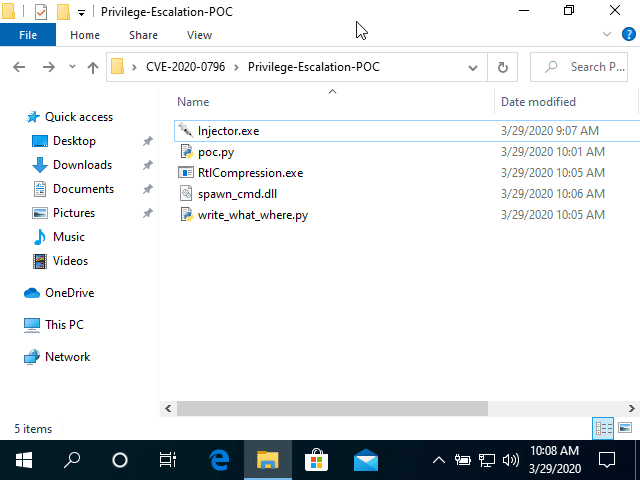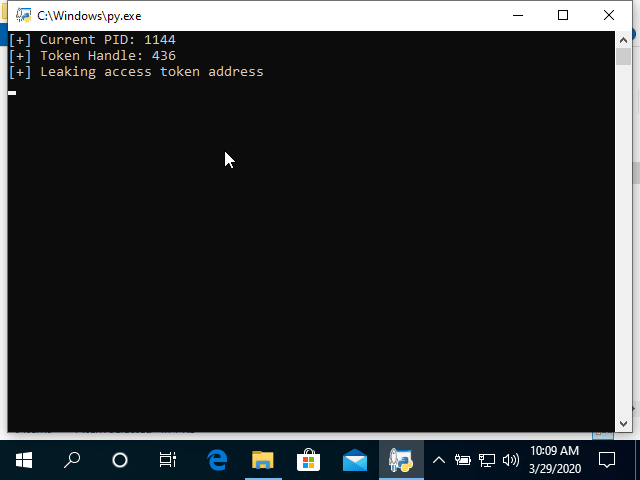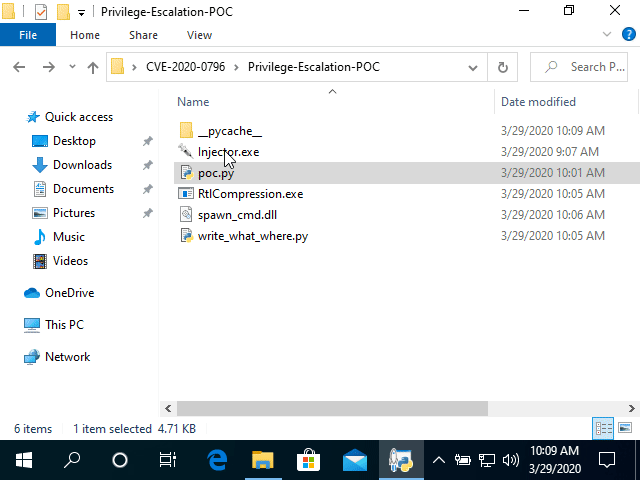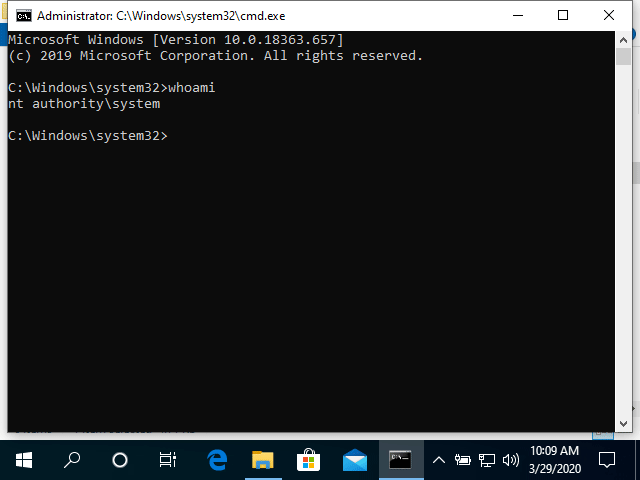
Microsoft soon released the SMBGhost patch for all affected versions and things seemed to settle then. But on June 9, 2020 cybersecurity researchers from ZecOps have identified a new critical vulnerability that’s related to SMBGhost, and has been dubbed as ‘SMBleed’.
What is SMB (Server Message Block)?
Server Message Block is a network communication protocol, that helps connect client and server for sharing and providing access to serial ports, printers, files and more. Mainly used by Windows-based machines, it works for computers connected on the same network or domains.
SMBleed SMB Vulnerability: Explained
Like its predecessor, SMBleed affects Server Message Block communication protocol and allows threat actors to leak kernel memory remotely. Classified as CVE-2020-1206, the bug takes advantage of SMB’s decompression function
This news has come in shortly after the SMBGhost exploit code was made public last week in a new POC. CISA (Cybersecurity and Infrastructure Security Agency) advised the users to update their Windows 10 machines as soon as possible.
It seems that ALOT of people are interested in the #SMBGhost CVE-2020-0796 RCE PoC source. Since @ZecOps will be releasing theirs in the coming days, and the bug has been patched for months, I think its OK to release for educational purposes. Find it here:https://t.co/6rA7yPCkeA https://t.co/NVkyKu6UMf
— chompie (@chompie1337) June 2, 2020
SMBleed vulnerability arises from the decompression ‘Srv2DecompressData’ function process (similar to SMBGhost) in the SMB ‘srv2.sys’ server driver. The client sends a compressed message, which is decompressed by Srv2DecompressData while allocating required memory space. But the said function fails while handling malicious requests (such as SMB2 Write), meant for the victim SMBv3 Server. This allows the threat actor to:
- Read uninitialized Kernel memory
- Edit compression function
Researchers further explain,
“The message structure contains fields such as the amount of bytes to write and flags, followed by a variable length buffer. That’s perfect for exploiting the bug, since we can craft a message such that we specify the header, but the variable length buffer contains uninitialized data.”
You can find the SMBleed PoC source code here.
SMBleedingGhost: Chaining SMBleed & SMBGhost
SMBGhost was an extremely severe vulnerability, with an intense score of 10 CVSS. Thus, combining these 2 inter-linked vulnerabilities together will prove to be a catastrophe.
ZecOps team has confirmed that using SMBleed in conjunction with SMBGhost allows the hacker to launch Remote Code Execution (RCE) attacks. Here’s the PoC source code for research and educational purposes only.
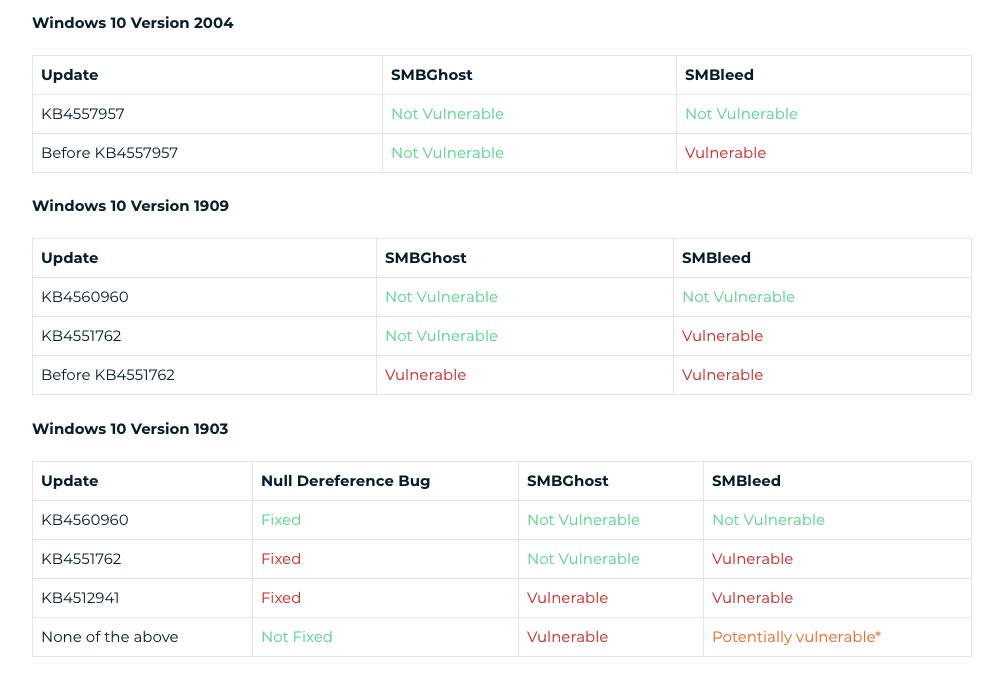
SMBleed Affected Windows Versions
SMBleed and SMBGhost impacts Microsoft Windows 10 systems:
- Version 2004
- Version 1909
- Version 1903
Here’s a complete summary of all affected versions and their updates w.r.t SMB vulnerabilities:
CVE-2020-1206 SMBleed Patch
Fortunately, SMBleed vulnerability news came out after Microsoft released its patch in June 2020 Patch Tuesday. We strongly recommended everyone with unpatched machines to install the recent Windows update as soon as possible.
For those, whose machines are not covered in the update, please follow the below instructions to stay safe from SMBleed/ SMBGhost attacks:
- Block Port 445 to stop lateral movements
- Enable host isolation
- Disable SMB 3.1.1 compression
To read Microsoft’s documentation of SMBleed click here, for SMBGhost click here.
To read ZecOps full technical article on SMBleed Vulnerability, click here.
Follow us on Telegram and Twitter for all such latest cybersecurity news and updates.